John shares his iPhone Home Screen and Jonathan has a new automation toy, plus the usual Links, App Debuts, the latest happenings in the Club MacStories+ Discord community, and a recap of MacStories articles and this week’s episodes of MacStories podcasts....
 Previously, On MacStories
Previously, On MacStories
Stories What’s in My WWDC 2024 Bag? Apple TV Go: How a USB-C Mod Spiraled into an iPad-Based tvOS Workstation Controller for HomeKit’s Interactive Floor Plan Is the Best Way to Control Your Home Yet Apple Highlights Its 2023 Developer Programs Announcing the Club MacStories WWDC Discount Apple Design Award Winners Announced Comfort Zone Debuts...
 Previously, On MacStories
Previously, On MacStories
Stories Kino First Impressions: An iPhone Video Camera App from the Makers of Halide 2024 ADA Finalists Announced Apple Announces WWDC 2024 Details Podcasts MacStories Unwind: The MacStories Unwind 2024 Apple Music Playlist Magic Rays of Light: tvOS Wishes 2024 and Franklin Ruminate, Episode 185 – I’ll Eat Glue Cheese AppStories, Episode 385 – Our...
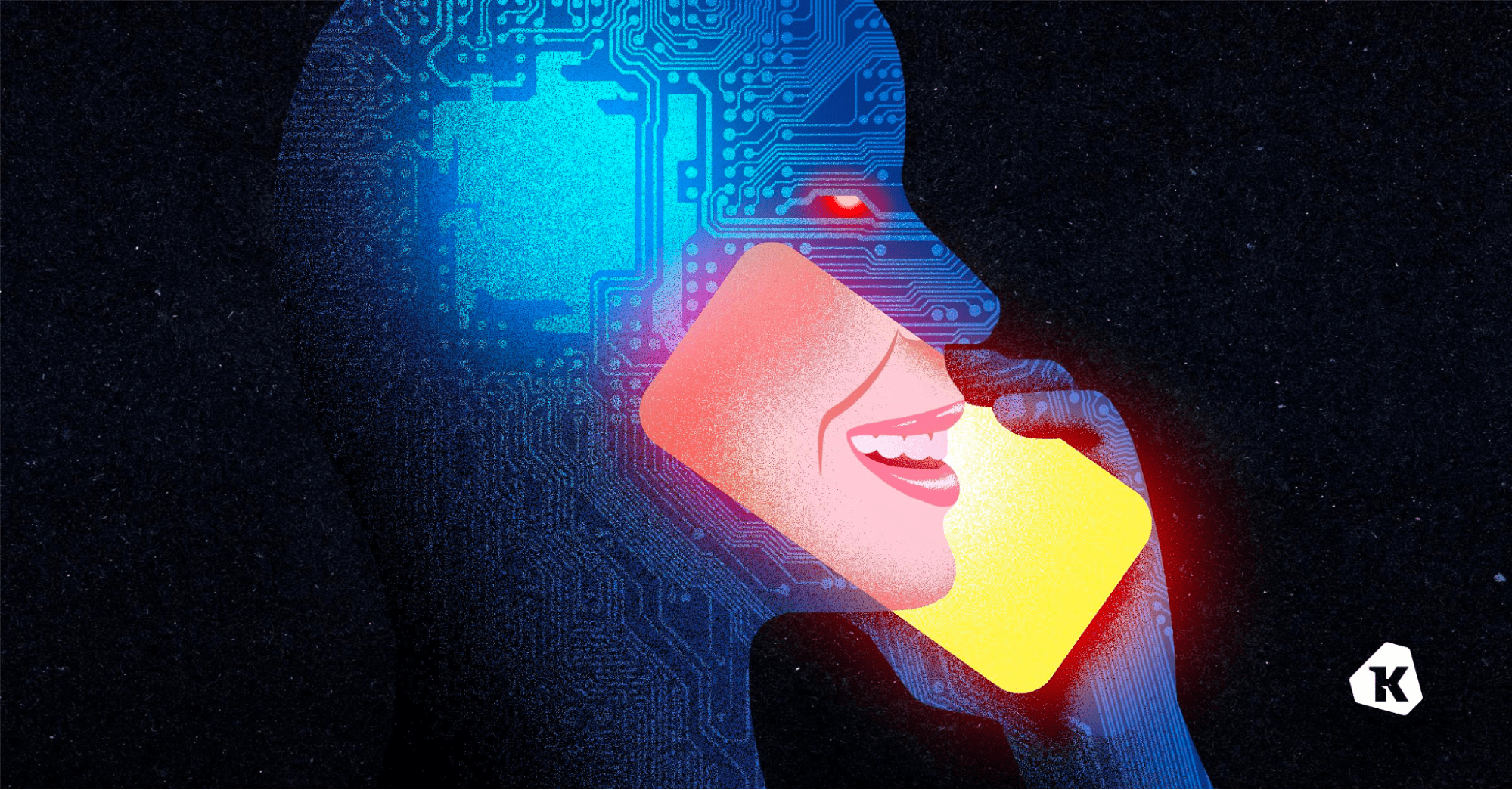
Voice Clones Have Crossed the Uncanny Valley [Sponsor]
Now, don’t get offended, but – you aren’t as good at clocking deepfakes as you think you are.
And it’s not just you–nobody’s that good at it. Not your mom, or your boss, or anyone in your IT department.
To make matters worse, you probably think you can spot a fake. After all, you see weird AI-generated videos of celebrities on social media and they give you that uncanny valley tingle. But it’s a different ballgame when all you’ve got to go on is a voice.
In real life, people only catch voice clones about 50% of the time. You might as well flip a coin.
And that makes us extremely vulnerable to attacks.
In the “classic” voice clone scam, the caller is after an immediate payout (“Hi it’s me, your boss. Wire a bunch of company money to this account ASAP”). Then there are the more complex social engineering attacks, where a phone call is just the entryway to break into a company’s systems and steal data or plant malware (that’s what happened in the MGM attack, albeit without the use of AI).
As more and more hackers use voice cloning in social engineering attacks, deepfakes are becoming such a hot-button issue that it’s hard to tell the fear-mongering (for instance, it definitely takes more than three seconds of audio to clone a voice) from the actual risk.
To disentangle the true risks from the exaggerations, we need to answer some basic questions:
- How hard is it to deepfake someone’s voice?
- How do hackers use voice clones to attack companies?
- And how do we guard ourselves against this… attack of the clones?
Like a lot of modern technologies, deepfake attacks actually exploit some deep-seated fears. Fears like, “your boss is mad at you.” These anxieties have been used by social engineers since the dawn of the scam, and voice clones add a shiny new boost to their tactics.
But the good news is that we can be trained to look past those fears and recognize a suspicious phone call–even if the voice sounds just like someone we trust.
If you want to learn more about our findings, read our piece on the Kolide blog. It’s a frank and thorough exploration of what we should be worried about when it comes to audio deepfakes.**
Our thanks to Kolide for sponsoring MacStories this week.
 Previously, On MacStories
Previously, On MacStories
Stories Apple Apologizes for Crush! Video Stu Maschwitz on the Filming of Apple’s Let Loose Event Apple Music Adds Shazam Radio Spins Charts and a New Industry Program Quinn Nelson of Snazzy Labs Explains the iPad Pro’s Tandem OLED Screen and the M4 Chip Marvel Studios and ILM Immersive Announce an Upcoming Vision Pro Project...
 Previously, On MacStories
Previously, On MacStories
Stories Federico Updates His Setup with the Lenovo Legion Go and More How to Load Your Game Boy Games Onto the iPhone to Play in the Delta Emulator Emulators Will Change the App Store Forever The Delta Videogame Emulator Launches on the App Store AltStore Is Now Available in the EU Soulver 3 for iOS:...
HomeKit Gadgets: The MacStories Team Collection
John: Everyone on the MacStories team is deep into HomeKit devices. For me, smart home gadgets tick all the boxes:
- Hardware
- Software
- Automation
It’s really as simple as that.
However, as fun as HomeKit devices can be, they can also be frustrating. The best accessories fit comfortably into your household, making life a little easier but falling back gracefully to a simple solution for anyone in your home who isn’t interested in automation. It sounds easy, but it’s a tough balancing act that few companies get right.
We’ve all tried our share of HomeKit and other smart home devices. Some have worked out, and others have fallen by the wayside as failed experiments. Today, we thought we’d pool our collective experience and share with you the MacStories team’s favorite smart home gadgets.
We have a lot of ground to cover, so this story will focus on indoor gadgets. Soon, we’ll shift our focus to the great outdoors.
Table of Contents
 In This Issue
In This Issue
Federico has a tip on getting the name of the frontmost Mac app using Shortcuts and shares ActiveTask, which creates a Things task that deep-links to an Obsidian document, Jonathan has created an Action Button-like automation for the Mac, John imagines the Apple game controller of his dreams, plus the usual Links, App Debuts, the...
 A Small Update to ThingsBox
A Small Update to ThingsBox
In December, I published an Automation Academy column for Club Plus and Premier members about ThingsBox, a comprehensive shortcut to quickly save all kinds of data into the Things inbox. I’ve been using ThingsBox myself for months now, and I love it, but earlier this week, I realized that it wasn’t properly saving URLs shared...